EC Council Training
EC Council Certification Training
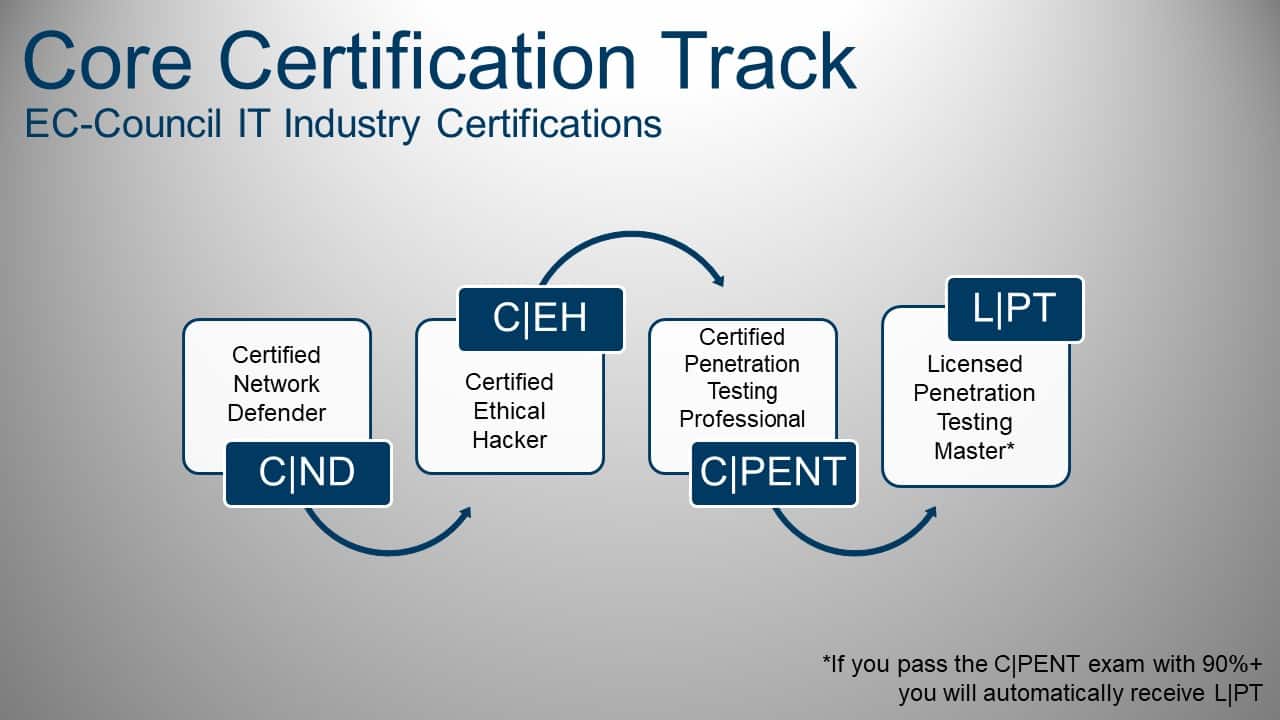
The International Council of E-Commerce Consultants (EC-Council) is a member-based organization that certifies individuals in various e-business and information security skills.
International Council of E-Commerce Consultants, also known as EC-Council, is the world’s largest cyber security technical certification body. With over 200,000 certified information security professionals globally, they have influenced the cyber security mindset of countless organizations worldwide.
Upcoming Classes
If you need assistance please CONTACT US