Email Threats
Email Threats
According to Cisco Talos, about 8 billion spam emails are sent out in the US alone each day. Of those, over 1 billion request the recipient to “click-this-link” as their method of deception.
How Can I Tell Genuine and Suspicious Emails Apart?
A typical phishing email is one that appears to be from a trusted source but is, in fact, a fraudulent communication with one goal: to do harm. It fits under the category of social engineering, because the sender often tries to pressure the recipient into performing some form of action (opening an attachment, clicking a link, visiting a website, calling a number, etc.).
Often the kinds of pressure they put the recipient under, can relate to losing something if urgent action is not taken immediately: your account will be closed; or you may lose money of you don’t act right now, etc. The bad actors will try their best to fool you and make you perform the action they want you to take.
Let’s look at a specific instance...
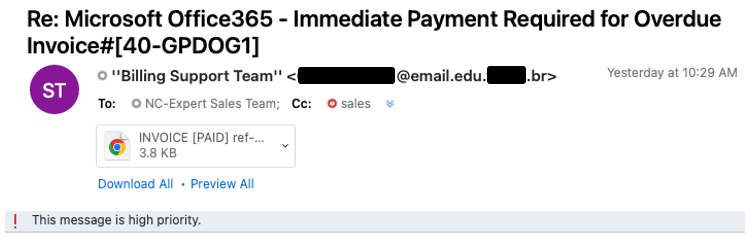
At first glance, if you are in a hurry to get things done, you may click the attachment. Once you do that you could be in for a world of hurt.
Let’s analyze this specific email...
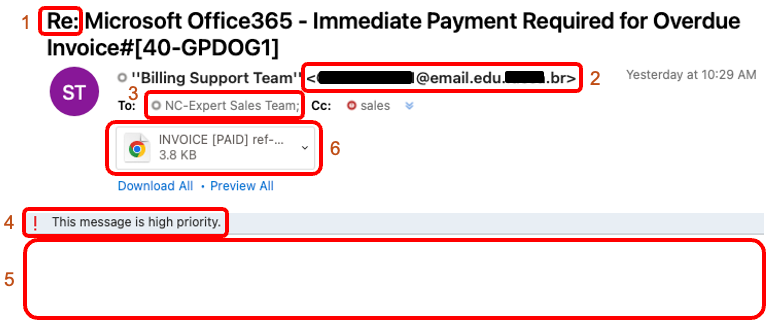
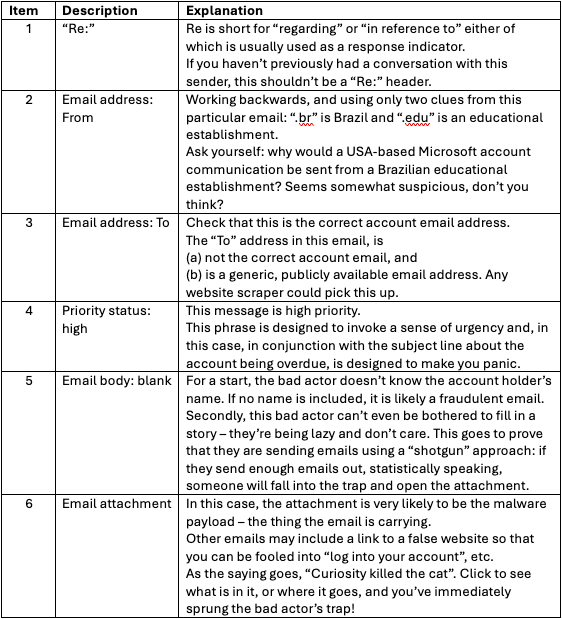
The following is a description of the suspicious clues in this email...
Looking at other examples...
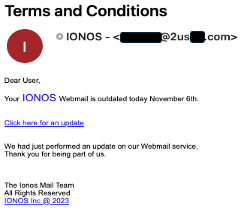
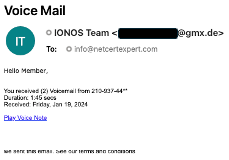
These emails are instantly identifiable as not being from the vendor they purport to represent. Simply look at the “From” email addresses, and you can be confident in ignoring them... without clicking on the included links. Additionally, neither of the emails refer to the account holder by name – because they don’t know it. Small, simple things like these can give big clues as to whether the email is genuine or not.
Some senders actually make an effort to try to have their emails look something like the real thing. This employee was not expecting any DocuSign agreements...
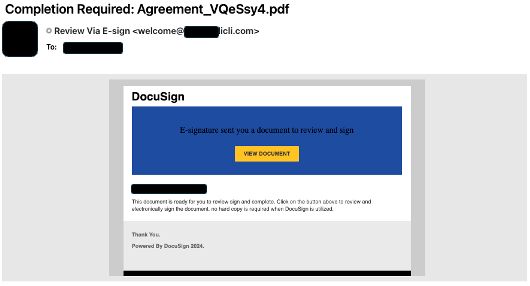
The email was sent to a specific employee (hence the blacked-out text), but because the employee was suspicious, they did not click on the button.
Other things to look out for are:
- Emails to generic recipients. These salutations can include “Dear account holder” “To Whom it may Concern”, it may include all or part of the recipient’s email address, or it may not be addressed to a specific recipient at all.
- Grammatical errors. If you read the email body text aloud, the sentence structure may sound a bit strange. Sentences may start with lowercase letters. There may be additional spaces between the words within a sentence.
- Misspelled words. Spelling can be another give-away. Simple words may be spelled incorrectly but these might be missed if you read the email quickly or simply give the sender the “benefit of the doubt”. Professional emails usually go through quality assurance checking to ensure that words are spelled correctly and that the sentence structure is sound.
- Font. There is a difference between the letter a and the letter a. The difference is subtle to the human reader, but can be very distinct to a computer. Additionally, if you see changes in the font as the email text progresses, especially if specifics about you/your company are included using that different font, there is a good chance that the sender has used automation to insert those details thus indicating that this is likely a spam email.
- URLs and Email Addresses. Look for odd spelling in URLs and email addresses. For example, “microsoft” may be spelled “rnicrosoft”. On first glance they may look the same, but they are vastly different – one starts with an “m”, the other starts with r followed by n. Additionally, look for strange or out-of-place prefixes and suffixes.
If something seems amiss, trust yourself. Your intuition may be saving you from a very negative experience.
What Kinds of Threats Can Phishing Emails Carry?
Of the billions of phishing emails sent out each day, a large number use the request to “click this” as their method of deception. The click can do a multitude of things from taking you to a website, to downloading malware onto your device.
One trick they may use to fool you into clicking on their link is to include a “convenient” return email link within the body of the email. This is not necessarily a link to make it easier for your email system to respond to the incoming email, rather, it is likely to be a link to a malicious URL. Additionally, you may miss the fact that the response link within the email is addressed to a different email account than the one from which the email was sent. This is another suspicious marker, as is the case here...
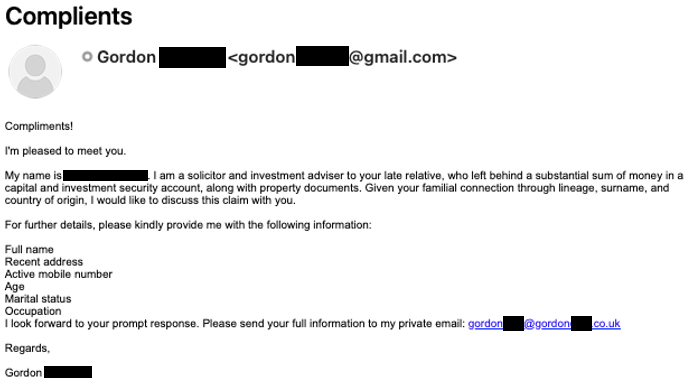
Either by visiting a malicious website, or inadvertently downloading malicious code, there are a number of end results the bad actor is looking to achieve:
- Install malware. Malware is a malicious program that, once installed can open your system to spyware, viruses, trojans, or any of a number of unwanted programs.
- To acquire data. Data from your system can be downloaded to a local computer or anywhere the bad actor defines.
- Money. They could disable and lock your system until a ransom has been paid. Even if you pay, the statistics infer that you almost certainly will never see all your data again.
- Impersonation. The bad actor might want to use your corporate identity to obtain (steal) important company data.
Zero Trust
There is an old Russian proverb which states, “Doveryay, no proveryay,” or “Trust, but verify”. Suzanne Massey, a Russian history scholar, famously taught this to US President Ronald Regan, who used it during his term in office (which was when it came into common usage in the United States). This refers to being polite, but double-checking everything. Don’t accept anything on face value. This is very good advice with regard to cyber security.
It is better to be overly suspicious than to be susceptible. If you don’t recognize a sender, or even if you do, but you weren’t expecting information from them, don’t click any attachments, links, or on any included-in-the-text-body email addresses. If you know the sender, pick up the phone and check with them. It may be that they didn’t know their email was being used without their knowledge... or it could be a genuine email and attachment. It is better to be sure.
If you have a reminder about and overdue payment, or some other account problem, log into your account, and check it from there. Call your bank, and check with them: is there a problem with my mortgage/rent/monthly payment? Be paranoid.
Sometimes people are rushed, stressed, and tired. It is during these times, when deadlines are looming, that we may not pay as much attention as we should. It only takes one click of a mouse button to start a snowball rolling which could cost the company millions of dollars and receive a serious knock to its reputation.
In its 2023 Data Breach Investigations Report, Verizon noted that nearly 75% of all breaches are caused by human error (mistakes, or succumbing to social engineering tactics, etc.). With this in mind, can you guarantee that your employees will never lose concentration for a moment and inadvertently click a link in an email? Do you trust your employees 100% with the entire security, financial well-being, and reputation of your organization? Or do you think they should be made aware of potential hazards and pitfalls? It’s certainly something to think about.
====
How We Can Help
To begin the process of training your employees in cybersecurity procedures as efficiently and cost-effectively as possible, NC-Expert provides you with a 1-day starter training session: CyberSAFE. ( https://www.nc-expert.com/class/certnexus-cybersafe )
In this training, your team will be taught the basics of cyber security, and will be made aware of the fundamental traps into which many employees fall, inadvertently allowing attackers access into your system.
Once this training has been completed, we can provide further trainings, which increase in complexity as your employees progress up the access permissions chain.
We can provide standard training classes or can customize a program to suit your specific needs and budget. Our trainings are delivered by expert instructors, for individual employees (in our public classes) or for private groups, virtually/online (in real time) or at your site. Contact us for details.
You are welcome to visit our website homepage: https://www.nc-expert.com/
Or you can view our Security training portfolio here:
https://www.nc-expert.com/training-classes-by-track#NetworkSecurity
...
About NC-Expert
NC-Expert is a privately-held California corporation and is well established within the Wireless and Cyber Security industry certification training, courseware development, and consulting markets.
NC-Expert has won numerous private contracts with Fortune level companies around the world. These customers depend on NC-Expert to train, advise, and mentor their staff.
If you are looking for the best in IT industry training then call us at
(855) 941-2121 or
contact us by email today.
This post appeared first on NC Expert .
NC-Expert Blog





